- Our goal is to put in place a support system that encompasses Information Technology (I.T.), data encrypted security, and a fully trained network resiliency staff.
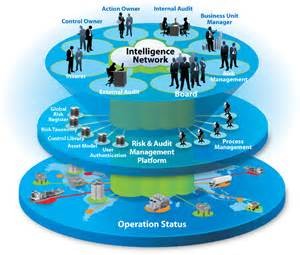
- To develop a test, and maintenance I.T. disaster recovery plan, better secure the telecommunication systems, and infrastructure in the event of a disaster or business disruption.
- Our company will provide a comprehensive step-by-step IT disaster recovery plan, development methodology, and present key IT availability planning concepts. [email protected]
- This service will include various recovery techniques, strategies, and practical methods that will help you to build a robust resilient technology support infrastructure, as well as critical process recovery capabilities to ensure a fast efficient recovery of business operations, mission critical IT systems, applications, and data.

- Organizations are continuously challenged with protecting business critical applications and data.
- Even the slightest downtime in today’s data driven environment can do irreparable damages to businesses.
- Unexpected disasters and hardware failures can potentially render all data useless.

The need to respond to emergencies, accidents or natural disasters with minimal or no interruptions to your business operations is critical, from implementation to management.
